In June this year, the BlackSuit group deployed a ransomware attack against CDK Global, a leading provider of software solutions to some 10,000 car dealerships. The initial attack encrypted critical data and disrupted CDK’s service, effectively crippling the entire network.
While CDK was recovering, BS launched the second attack, further escalating the disruption. The compound effect forced the company to shut down the systems, blocking vital access to over 10,000 dealerships. They could not access sales, financing, parts ordering and customer management systems.
The breach achieved two primary goals: encrypt data and exfiltrate sensitive data. Attackers obtained names, addresses, phone numbers, and potentially even Social Security numbers and financial data.
Here’s the ransom note that arrived at CDK Global:
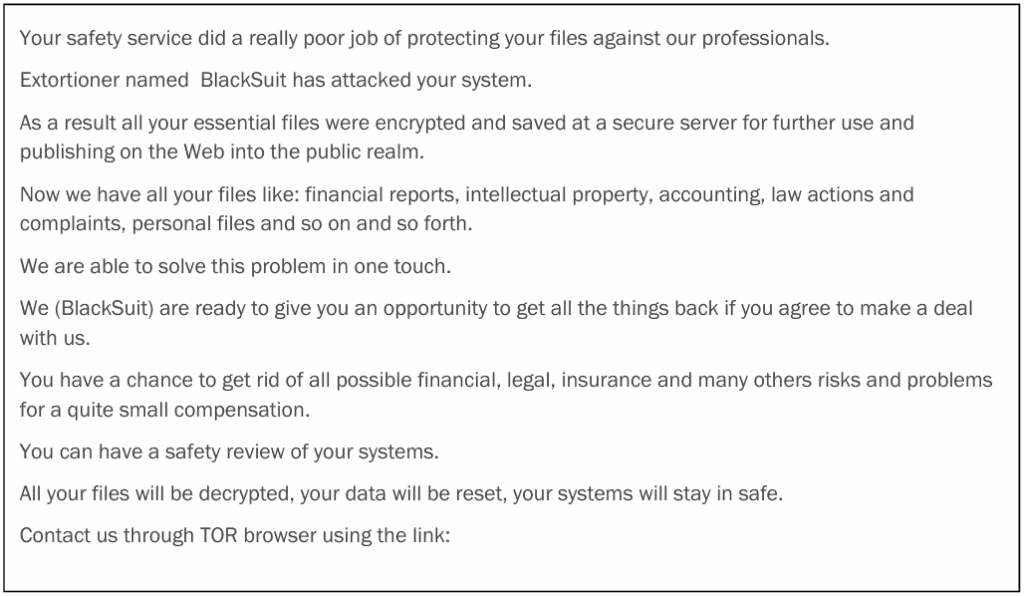
The effectiveness of the attack and hopelessness of the situation is evidenced by the fact that only two days later, CDK Global paid $25 million in Bitcoin, the second-largest ransom paid to date.
This incident highlights the supply chain vulnerability; especially when it relies on third-party providers. A single attack can have a cascading effect. Furthermore, it underscores the seriousness of ransomware attacks. They cripple operations and inevitably lead to serious financial losses.
Table of Contents
- Responsibilities of a Chief Technology Officer in Cybersecurity
- Understanding the Threat Landscape
- List of Reliable Cybersecurity Threat Intelligence Sources & Tools
- Considerations
Responsibilities of a Chief Technology Officer in Cybersecurity
As a Chief Technology Officer, it can be your responsibility to ensure robust cybersecurity measures that, by default, include:
- Zero-Trust Policy w/ Multifactor Authentication
- Incident Response Plan
- Data Backups and Redundancy Systems
- Network Comparmalisation
- Employee Training (ie, establishing a security-conscious culture)
Your organisation requires a layered security strategy and approach to protect against multiple attack vectors. An IRP, data backups and recovery are just one part of that effort. The cybersecurity strategy must also include third-party risk management. And monitoring the evolution of the threat landscape is the only way to achieve both goals.
Understanding the Threat Landscape
If you are familiar with the mechanism of multi-vector attacks and the utilisation of Gen AI in cyberattacks, you can skip to the list of reliable intelligence sources. If not, read on because understanding the threat landscape and attack mechanisms is the prerequisite for an effective defence strategy.
We will use the CDK Global attack as an example because the BlackSuit group utilised various techniques and tools to achieve their goals.
BlackSuit ransomware is the evolution of the ransomware previously identified as Royal ransomware, which was used from approximately September 2022 through June 2023. Royal was best known for the attack against the City of Dallas’ systems in May 2023.
The CDK attack used partial encryption, allowing the threat actor to choose a percentage of data to encrypt. This method lowers the encryption percentage for larger files, effectively helping to evade detection. But that was just one side of the attack. BlackSuit also engaged in double extortion, threatening to reveal stolen data if CDK refused to pay the ransom.
The million-dollar question in these types of security breaches is always the same: how did the threat actor gain access to the network?
Gaining the Initial Access
In the case of BS, they commonly gain access via phishing emails. Victims unwittingly install the delivery system. Another technique they use is RDP (Remote Desktop Protocol) compromise. In some instances, BlackSuit actors exploited vulnerabilities in public-facing applications or leveraged initial access brokers to gain initial access and source traffic by harvesting VPN credentials from dealer logs. In this case, however, a likely scenario is that the threat actor gained access via a compromised dealer network.
Once they gained access, the attack unfolded in several stages:
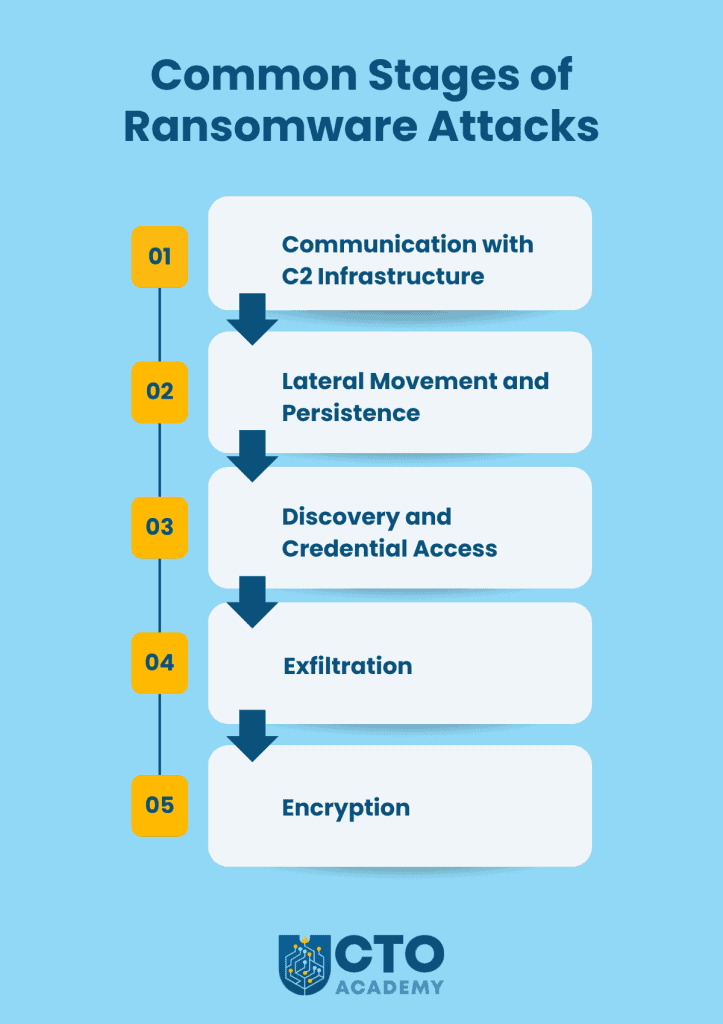
- Communication with C2 infrastructure (Command & Control) to download multiple tools using legitimate software (eg, Chisel, SSH client, OpenSSH, PuTTY, MobaXterm…).
- Lateral movement and persistence by using legitimate OS diagnostic tools (eg, RDPs and RMMs such as PsExec) and then utilising Gootloader and SystemBC to load additional tools and maintain persistence.
- Discovery and credential access using SharpShares and SoftPerfect NetWorx to enumerate victim networks and then Mimikatz and Nirsoft to steal credentials.
- Exfiltration (CobaltStrike for penetration and then Ursnif/Gozi, RClone and/or Brute Ratel for aggregation and exfiltration).
- Encryption. Before encrypting files, they check if the Windows Restart Manager is using or blocking the file. If not, they execute the Windows Volume Shadow Copy service (vssadmin.exe) to delete shadow copies and inhibit system recovery.
Common Indicators of Compromise
- Numerous batch (.bat) files on infected systems in directories:
- C:\Temp\
- C:\Users\<user>\AppData\Roaming\
- C:\Users\<users>\
- C:\ProgramData\
- Root C:\ directory
- C:\Users\Public\conhost.exe client 149.28.73.161:443 R:149.28.73.161:43657:socks (traffic tunnelling technique using Chisel)
- royal_w (encryption extension)
- InstallerV20.8.msi
- Windows_encryptor.exe…
(For the complete list of IOC, check this CISA document.)
Evolving Threat with the Help of Gen AI
There are several ways threat actors utilise Gen AI in cyberattacks:
- Enhanced malware development (polymorphic, targeted and evasive binaries).
- Automated social engineering (sophisticated phishing, deepfakes/impersonation, manipulative chatbots…).
- Accelerated vulnerability detection (ie, automated scanning and predicting exploits).
- Circumventing security measures (CAPTCHA bypass, evading biometric authentication by generating synthetic data…).
- Amplifying ongoing/existing attacks (scaling through automation, increasing complexity…).
Mitigation Strategies
- AI-powered defence (eg, leveraging GenAI for defensive purposes, such as threat detection and analysis)
- Enhanced security awareness (educating users on how to identify AI-powered attacks)
- Collaboration (between security researchers, industry professionals and policymakers)
- Constant education and monitoring
List of Reliable Cybersecurity Threat Intelligence Sources & Tools
Threat Intelligence Gathering
Security Advisories
CISA – Cybersecurity and Infrastructure Security Agency; timely and actionable information about specific cybersecurity threats and vulnerabilities (ie, “alerts” about immediate dangers)
NIST – National Institute of Standards and Technology; guidance, standards, and best practices for cybersecurity (ie, the “rulebook” for building secure systems)
MITRE – MITRE ATT&CK (Adversarial Tactics, Techniques and Common Knowledge) + Common Vulnerabilities and Exposures (CVE) database; adversary tactics and techniques based on real-world observations
ENISA – European Union Agency for Cybersecurity; advisories, reports, and best practices for cybersecurity in the European Union
NCSC – National Cyber Security Centre – UK; guidance, advisories and support for organisations in the UK
CERT/CC – Computer Emergency Response Team/Coordination Center; vulnerability information and incident response support
OWASP – Open Web Application Security Project; web application security and resources like the OWASP Top 10 vulnerabilities and cheat sheets
CSA – Cloud Security Alliance; guidance and best practices for cloud security, including the Cloud Controls Matrix (CCM)
SHADOW SERVER FOUNDATION – a non-profit organisation that gathers and analyses internet threat data, providing reports and advisories
Researchers and Blogs
krebsonsecurity.com – Cybercrime, data breaches and online fraud
schneier.com – A wide range of security topics with insightful analysis
troyhunt.com – Data breaches and online security
threatpost.com – Up-to-date news and analysis on cybersecurity threats, vulnerabilities and malware
Secureworks Threat Analysis – In-depth threat research, analysis and reports on emerging threats
unit42.paloaltonetworks.com – Threats, vulnerabilities and attack techniques analyses
googleprojectzero.blogspot.com – Finding and reporting zero-day vulnerabilities
thedfirreport.com – Incident response reports and analysis of real-world cyberattacks
sans.org – Cybersecurity training and research, with blogs and resources on security topics
talosintelligence.com – Cisco’s threat intelligence organisation
Trellix – Threat detection and response, threat reports
Sekoia.io blog – Research reports and threat intelligence
Sentinel One blog – Security-related guides and threat intelligence
Bleeping Computer – Cybersecurity news, latest hacks, malware threats
Groups and Forums
Reddit’s r/cybersecurity – A subreddit for technical professionals to discuss cybersecurity news, research, threats, etc.
Wilders Security Forums – Malware analysis, security news and technical discussions
TechRepublic Security Forum – Active discussions on cybersecurity topics, including recent attacks and threats
Malware Labs Forums – Malware-related discussions, with sections on threat analysis and security news
Slack groups:
- CyberSec Professionals
- OWASP Slack
- SANS Blue Team Slack
Discord groups:
- Hack the Box Discord – For participants in the Hack the Box penetration testing platform, with discussions on challenges, techniques and security news
- TryHackMe Discord – For users of the TryHackMe platform, with channels for learning and discussing cybersecurity
- InfoSec Discord – A general cybersecurity Discord server with channels on various topics, including threat intelligence and security news
LinkedIn groups:
Other similar online communities:
- Stack Exchange Information Security – Q&A site for security professionals and enthusiasts, with a focus on technical questions and solutions
Vulnerability Management
Vulnerability Scanning Tools
Nessus by Tenable – Scans a wide range of assets, including operating systems, network devices, web applications and databases. Known for its excellent scanning speed, user-friendly interface and high accuracy.
QualysGuard by Qualys – A cloud-based vulnerability management solution that offers continuous scanning, vulnerability detection and prioritisation. Provides a centralised platform for managing vulnerabilities across your entire IT environment, including on-prem, cloud and mobile devices.
OpenVAS – An open-source vulnerability scanner that offers a comprehensive and regularly updated vulnerability database. Known for comprehensive vulnerability coverage, active community support and flexible deployment options.
Penetration Testing Tools
Metasploit Framework – A comprehensive penetration testing framework that provides exploits, payloads and auxiliary modules. It allows you to simulate attacks, identify vulnerabilities and gain access to systems. Open-source and commercial versions are available.
Burp Suite – A web application security testing tool for analysing and exploiting web vulnerabilities. It includes tools for intercepting and modifying HTTP requests, scanning for vulnerabilities and performing manual testing.
Nmap – A network scanning tool for discovering hosts, services and network vulnerabilities. It can perform various scans, including ping sweeps, port scans and OS fingerprinting.
Cobalt Strike – Often used by threat actors, its primary purpose is to simulate tactics, techniques and procedures (TTPs) of real-world attackers. CS establishes a C2 infrastructure, allowing pentesters to remotely control compromised systems. It provides a wide range of post-exploitation tools, enabling lateral movement within a network, escalating privileges, stealing data and deploying additional malware.
Bug Bounty Program Examples
HackerOne – One of the largest and most reputable bug bounty platforms, connecting businesses with a network of security researchers. They host programs for a wide range of companies, including major tech giants like Google, Microsoft and Intel, as well as government agencies and financial institutions.
Bugcrowd – Like HackerOne, this platform offers comprehensive vulnerability management, providing tools to triage, prioritise and remediate security threats.
Synack – Takes a more exclusive approach, vetting and onboarding security researchers through a rigorous process. The focus is on high-value targets and critical infrastructure.
YesWeHack – A European bug bounty platform with a growing global presence. Offers programs for a variety of organisations, with a focus on European companies and government agencies.
How Does It Work?
Bug bounty programs on specialised platforms incentivise ethical hackers to find and report vulnerabilities in your systems. You define the scope and rules and set reward levels. Researchers find vulnerabilities, report them to you and get paid bounties for valid findings. This helps you proactively improve your security posture by leveraging a much wider talent pool and paying only for results.
Threat Monitoring and Analysis
SIEM Tools
Splunk Enterprise Security – A leader in the SIEM space, known for its powerful data analytics and visualisation capabilities. Comes with advanced security monitoring, threat intelligence and incident response features. It’s highly scalable and can handle massive amounts of data.
IBM QRadar SIEM – Uses advanced correlation and analytics to identify complex attacks and provides automation capabilities to streamline incident response. It’s available as both an on-premises and cloud-based solution.
LogRhythm SIEM – Known for its comprehensive security analytics and user-friendly interface. Provides a wide range of features for threat detection, investigation and response, including real-time monitoring, anomaly detection and user behaviour analytics.
Rapid7 InsightIDR – A cloud-native SIEM solution for endpoint detection and response (EDR). It combines log management, user behaviour analytics and endpoint telemetry to provide a comprehensive view of security events. Well-suited for detecting insider threats and advanced persistent threats.
Threat Intelligence Platforms
Recorded Future – Extensive threat intelligence collected from open, closed and technical sources, including the dark web. The platform excels in predicting future threats and providing context for security events.
CrowdStrike Falcon X – Combines threat intelligence with endpoint detection and response (EDR) capabilities. It provides real-time threat analysis, adversary profiling and automated threat hunting.
Anomali ThreatStream – A cloud-based platform for collecting, analysing and sharing threat intelligence. It allows you to integrate threat data from various sources, automate threat analysis and collaborate with other organisations.
Mandiant Threat Intelligence – Now part of the Google Cloud, Mandiant provides curated threat intel using human and artificial intelligence. Intel is compiled by 500+ threat analysts who respond to cyber-attacks and open-source threat intel (OSINT).
Network Traffic Analysis Tools
SolarWinds Network Performance Monitor (NPM) – A network monitoring and management tool that provides deep visibility into network traffic, performance and availability. It offers real-time monitoring, alerts and detailed reports to help you identify and troubleshoot network issues.
ManageEngine OpManager – Provides real-time visibility into network traffic, performance and device health. It offers features like bandwidth monitoring, network mapping and application performance monitoring.
PRTG Network Monitor – A versatile network monitoring tool that offers a wide range of sensors for monitoring various aspects of your network, including bandwidth usage, network devices and applications. It provides real-time monitoring, alerts and customisable dashboards.
Wireshark – A powerful open-source network protocol analyser for capturing and analysing network traffic in detail. It provides deep packet inspection capabilities and a wide range of filters and analysis tools.
Considerations
The weakest links in every cybersecurity chain are:
- Users
- Unpatched/outdated systems
It’s not uncommon for former employees to access shared networks with year-old credentials even though systems got updated in the meantime.
It comes down to proper digital hygiene in cybersecurity as Bryan Seely, a cybersecurity expert and ethical hacker, said in one of the live sessions hosted by CTO Academy. These are those small seemingly invisible doors hackers use to gain initial access and deliver payloads.
What’s worse, social engineering is becoming an approach of choice for threat actors because it’s easier to trick a human than a network system.
Add remote and hybrid working environments and you have a recipe for disaster because users are accessing networks through home routers. How many of them do you think changed the default login credentials on their modems and routers? All you have to do is come near enough to catch the signal, punch in defaults and you are in control of the user’s home network. A quick vulnerability scan and the door to the company’s network is wide open. A simple keylogger in a critical device will suffice if there’s no multifactor authentication.
So start by enforcing a zero-trust policy and strong multifactor authentication (avoid SMS-based 2FA). If possible, make it mandatory to use a secure VPN when accessing sensitive data or connecting to critical parts of the company’s network. Ensure also that your network is properly compartmentalised (check the latest BT attack to see the advantages). And by all means, establish regular employee education in social engineering and phishing scams. Keep them updated but more importantly, highly engaged.
Make no mistake; even these baby steps can prevent a serious breach. But these are war games after all so arm yourself with the necessary intel and tools.

